**Problem: I’m trying to deploy hosts in an IPv6-only environment. I’ve configured a isc dhcpd for announcing dns bootfile-url which is http://[2001:638:902:200f:139:18:16:90]/unattended/iPXE . The Apache of Foreman is answering with an 404 and “Host unknown” no matter if iPXE loader or curl from a booted environment. When i the same with a IPv4 host - all fine. **
Expected outcome:
Foreman and Proxy versions: 1.16
Foreman and Proxy plugin versions:
**Other relevant data:
/var/log/foreman/production.log:
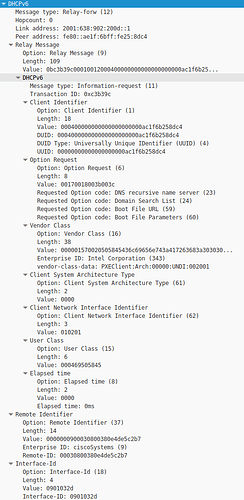
2018-03-13 12:04:52 9bf4bf3c [app] [I] Started GET "/unattended/iPXE" for 2001:638:902:200d:ae1f:6bff:fe25:8db8 at 2018-03-13 12:04:52 +0100
2018-03-13 12:04:52 9bf4bf3c [app] [I] Processing by UnattendedController#host_template as TEXT
2018-03-13 12:04:52 9bf4bf3c [app] [I] Parameters: {"kind"=>"iPXE"}
2018-03-13 12:04:52 9bf4bf3c [app] [I] Current user: foreman_api_admin (administrator)
2018-03-13 12:04:52 9bf4bf3c [app] [D] Setting current user thread-local variable to foreman_api_admin
2018-03-13 12:04:53 9bf4bf3c [app] [E] unattended: unable to find a host that matches the request from 2001:638:902:200d:ae1f:6bff:fe25:8db8
2018-03-13 12:04:53 9bf4bf3c [app] [I] Rendered text template (0.0ms)
2018-03-13 12:04:53 9bf4bf3c [app] [I] Filter chain halted as :get_host_details rendered or redirected
2018-03-13 12:04:53 9bf4bf3c [app] [I] Completed 404 Not Found in 15ms (Views: 4.5ms | ActiveRecord: 1.0ms)
host configuration:
---
parameters:
hostgroup: urzospoc
foreman_subnets:
- name: URZOSPOC-V814-IPv6
network: '2001:638:902:200d::'
mask: 'ffff:ffff:ffff:ffff::'
gateway: ''
dns_primary: ''
dns_secondary: ''
from: ''
to: ''
boot_mode: Static
ipam: EUI-64
vlanid: ''
network_type: IPv6
description: ''
foreman_interfaces:
- ip:
ip6: 2001:638:902:200d:ae1f:6bff:fe25:8db8
mac: ac:1f:6b:25:8d:b8
name: urzospoc01.dom.uni-leipzig.de
attrs:
mtu: 1500
netmask6: 'ffff:ffff:ffff:ffff::'
network6: '2001:638:902:200d::'
virtual: false
link: true
identifier: eno1
managed: false
primary: true
provision: true
subnet:
subnet6:
name: URZOSPOC-V814-IPv6
network: '2001:638:902:200d::'
mask: 'ffff:ffff:ffff:ffff::'
gateway: ''
dns_primary: ''
dns_secondary: ''
from: ''
to: ''
boot_mode: Static
ipam: EUI-64
vlanid: ''
network_type: IPv6
description: ''
tag:
attached_to:
type: Interface
- ip: 172.18.22.94
ip6: ''
mac: ac:1f:6b:29:37:05
name: ''
attrs:
enabled: true
ipaddress_source: DHCP Address
ptr: urzospocmgmt01.rz.intern.uni-leipzig.de
subnet_mask: 255.255.255.0
gateway: 172.18.22.254
1_ipaddress_source: DHCP Address
1_ipaddress: 172.18.22.94
1_ptr: urzospocmgmt01.rz.intern.uni-leipzig.de
1_subnet_mask: 255.255.255.0
1_macaddress: ac:1f:6b:29:37:05
1_gateway: 172.18.22.254
virtual: false
link: true
identifier: ipmi
managed: false
primary: false
provision: false
subnet:
subnet6:
tag:
attached_to:
type: BMC
provider: IPMI
username: ADMIN
password: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
domainname: dom.uni-leipzig.de
foreman_domain_description: ''
owner_name: Vadim Bulst
owner_email: vadim.bulst@uni-leipzig.de
ssh_authorized_keys: []
foreman_users:
admbulst:
firstname: Vadim
lastname: Bulst
mail: vadim.bulst@uni-leipzig.de
description: ''
fullname: Vadim Bulst
name: admbulst
ssh_authorized_keys: []
root_pw: "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
foreman_config_groups: []
puppetmaster: urzlxdeploy.rz.uni-leipzig.de
puppet_ca: urzlxdeploy.rz.uni-leipzig.de
foreman_env: development
enable-puppetlabs-pc1-repo: 'true'
keyboard: de
ntp-server: 139.18.1.2
time-zone: Europe/Berlin
classes:
environment: development
iPXE-Template:
#!gpxe
kernel http://suse.uni-leipzig.de/pub/centos.org/7.4.1708/os/x86_64/images/pxeboot/vmlinuz ks=http://urzlxdeploy.rz.uni-leipzig.de/unattended/provision?token=1188bb06-9709-4a46-9f23-054b8c876f6b&static=yes ip=dhcp
initrd http://suse.uni-leipzig.de/pub/centos.org/7.4.1708/os/x86_64/images/pxeboot/initrd.img
boot
**
[e.g. logs from Foreman and/or the Proxy, modified templates, commands issued, etc]