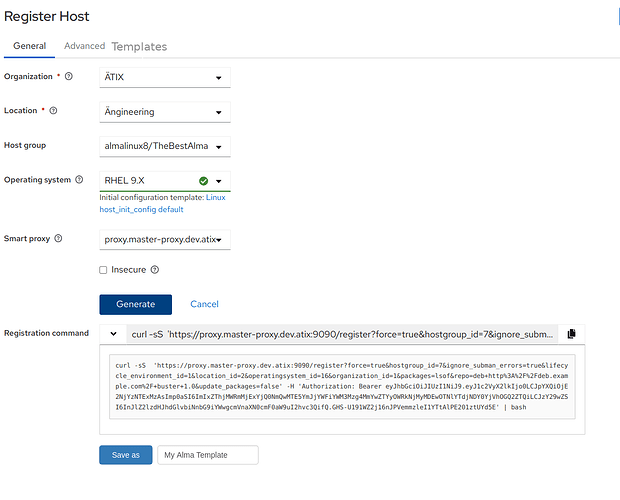
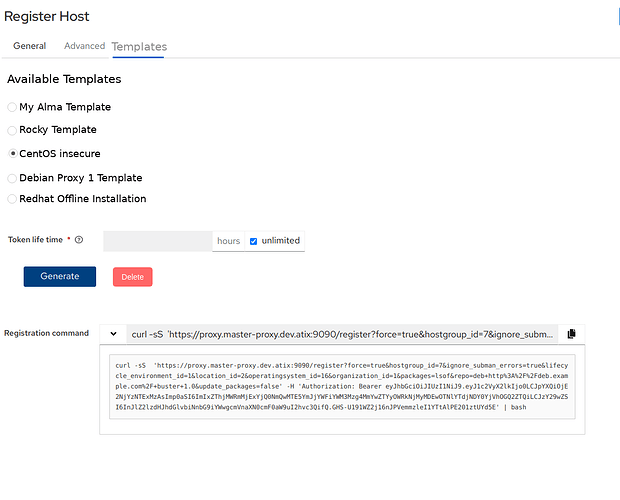
Please have a look at these 2 screenshots. This is, how I would simply improve the register host functionality:
- its possible to store the registration parameters in a extra db table called “register_host_templates”.
- on the new tab “templates”, templates are shown
- if you scroll over the template, it will show its configuration like “Organization: ÄTIX, Host Group: …”
- you can select a template, and then generate the register host curl again which will create a new token.
- its possible to delete an entry
Your thoughts?