Problem:
“invalid user” error when attempting to login to Foreman after setting up LDAP auth connecting to Active Directory.
Expected outcome:
User should be able to login but logs indicate invalid user. It seems as if the account used to BIND to the AD is not being established.
Foreman and Proxy versions:
1.20.1
Foreman and Proxy plugin versions:
Other relevant data:
2019-01-08T19:54:09 [I|app|] Started POST "/users/login" for 10.41.32.103 at 2019-01-08 19:54:09 +0000
2019-01-08T19:54:09 [I|app|ce441] Processing by UsersController#login as HTML
2019-01-08T19:54:09 [I|app|ce441] Parameters: {"utf8"=>"✓", "authenticity_token"=>"rrCz4KnC2egnphRr04+GYMweY0j6O+MB44v+aZUb1EvR2Z/gZ+KStLoB61XznRlOcHliKicAhD6maNVOfm90IQ==", "login"=>{"login"=>"drew.bentley@domain.com", "password"=>"[FILTERED]"}, "commit"=>"Log In"}
2019-01-08T19:54:09 [D|app|ce441] Attempting to log into an auth source as drew.bentley@domain.com for account auto-creation
2019-01-08T19:54:09 [I|app|ce441] invalid user
2019-01-08T19:54:09 [W|app|ce441] Failed login attempt from 10.41.32.103 with username 'drew.bentley@domain.com'
2019-01-08T19:54:09 [I|app|ce441] Redirected to https://10.110.2.50/users/login
2019-01-08T19:54:09 [I|app|ce441] Completed 302 Found in 17ms (ActiveRecord: 4.9ms)
2019-01-08T19:54:10 [I|app|] Started GET "/users/login" for 10.41.32.103 at 2019-01-08 19:54:10 +0000
2019-01-08T19:54:10 [I|app|20b61] Processing by UsersController#login as HTML
2019-01-08T19:54:10 [I|app|20b61] Rendering users/login.html.erb within layouts/login
2019-01-08T19:54:10 [I|app|20b61] Rendered users/_welcome_box.html.erb (1.6ms)
2019-01-08T19:54:10 [I|app|20b61] Rendered users/login.html.erb within layouts/login (2.5ms)
2019-01-08T19:54:10 [I|app|20b61] Rendering layouts/base.html.erb
2019-01-08T19:54:10 [I|app|20b61] Rendered layouts/base.html.erb (0.8ms)
2019-01-08T19:54:10 [I|app|20b61] Completed 200 OK in 5ms (Views: 3.9ms | ActiveRecord: 0.2ms)
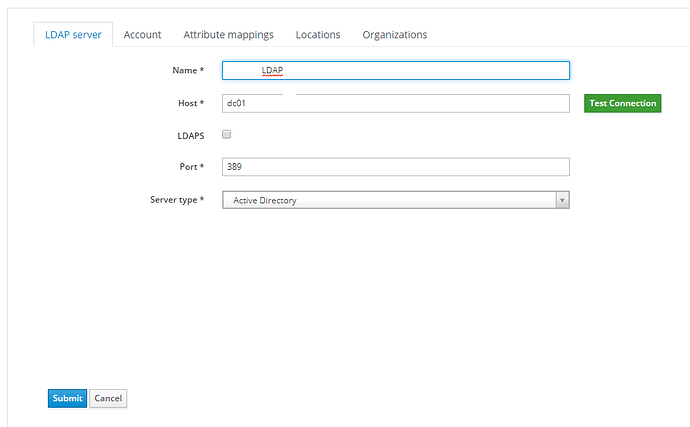
AD Test Connection works successfully using our defaults AD.GLOBAL on port 389.
I think the issue now is our AD required authentication to query the Active Directory LDAP. From my Windows Administrators, the only way to pass the username that works is the principleName format (username@domain.com).
I’ve verified from the command line on the same foreman host that I can do successful queries with ldapsearch command:
ldapsearch -x -D drew.bentley@domain.com -W -H ldap://ad.global -b "CN=L-HID-CHGVA-Foreman,OU=CHGVA,OU=Security,OU=SecurityGroups,OU=HID,OU=SSC,DC=ad,DC=global"
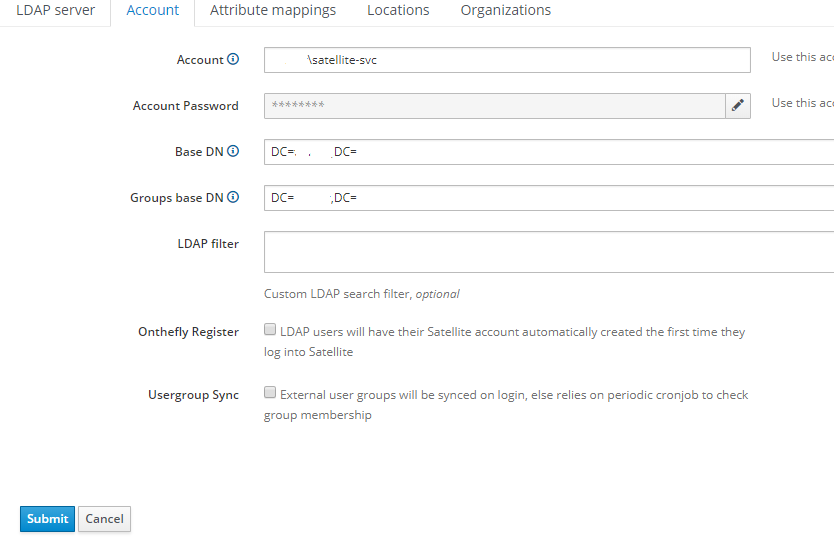
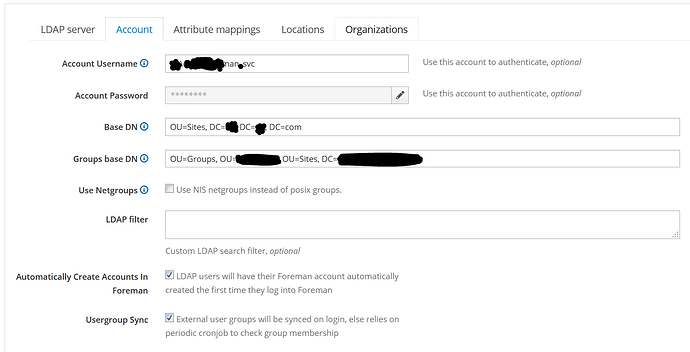
I’ve tried using AD.GLOBAL\username in the Account under LDAP Account and the drew.bentley@domain.com without success. Anything I try it appears as if the BINDING is never established.
The Foreman docs claim to use the DOMAIN\username for the account login for queries but if that’s the only method or string to pass, how can I get around this to auth with my full email or principle name to BIND to the AD server with.
Thanks for any suggestions, tips, etc.