I was able to capture some debug logs and also identified the failed tasks the external ID. Here is the log from that request:
2023-02-08T17:06:15 [I|app|8842882c] Started POST "/api/config_reports" for 10.160.236.27 at 2023-02-08 17:06:15 +0100
2023-02-08T17:06:15 [I|app|8842882c] Processing by Api::V2::ConfigReportsController#create as JSON
2023-02-08T17:06:15 [I|app|8842882c] Parameters: {"config_report"=>"[FILTERED]", "apiv"=>"v2"}
2023-02-08T17:06:15 [D|app|8842882c] Client sent certificate with subject 'puppetproxy.example.com' and subject alt names '["puppetproxy.example.com"]'
2023-02-08T17:06:15 [D|app|8842882c] CN and SANs were extracted from a client certificate.
2023-02-08T17:06:15 [D|app|8842882c] Verifying request from ["puppetproxy.example.com"] against [<list of smartproxies>]
2023-02-08T17:06:15 [D|app|8842882c] Processing report: {"host"=>"client.example.com", "reported_at"=>"2023-02-08 16:04:00 UTC", "status"=>{"applied"=>0, "restarted"=>0, "failed"=>0, "failed_restarts"=>0, "skipped"=>0, "pending"=>0}, "metrics"=>{"resources"=>{"changed"=>0, "corrective_change"=>0, "failed"=>0, "failed_to_restart"=>0, "out_of_sync"=>0, "restarted"=>0, "scheduled"=>0, "skipped"=>0, "total"=>385}, "time"=>{"anchor"=>0.000490885, "augeas"=>1.2025026129999998, "catalog_application"=>25.269473280990496, "concat_file"=>0.00048681699999999996, "concat_fragment"=>0.002981279999999999, "config_retrieval"=>14.841640418977477, "convert_catalog"=>0.639278615009971, "cron"=>0.000549198, "exec"=>0.20404195400000003, "fact_generation"=>88.66589018201921, "file"=>7.872653324999998, "file_line"=>0.015821999, "filebucket"=>8.6276e-05, "filesystem"=>0.086869895, "group"=>0.001864068, "logical_volume"=>0.526188599, "mount"=>0.006211277, "network_config"=>0.000745433, "network_route"=>0.000483817, "package"=>13.486791775000004, "plugin_sync"=>3.2444249549880624, "selboolean"=>0.029218056, "selinux_fcontext"=>0.000562644, "service"=>0.42916905499999997, "ssh_authorized_key"=>0.002704077, "total"=>134.12264593, "transaction_evaluation"=>25.185514822951518, "user"=>0.015191512000000002, "yum_cron_config"=>0.0063059200000000004}, "changes"=>{"total"=>0}, "events"=>{"failure"=>0, "success"=>0, "total"=>0}}, "logs"=>[{"log"=>{"sources"=>{"source"=>"Puppet"}, "messages"=>{"message"=>"Applied catalog in 25.27 seconds"}, "level"=>"notice"}}]}
2023-02-08T17:06:15 [I|app|8842882c] ForemanWebhooks::EventSubscriber: host_updated.event.foreman event received
2023-02-08T17:06:15 [D|tax|8842882c] Current organization set to none
2023-02-08T17:06:15 [D|tax|8842882c] Current location set to none
2023-02-08T17:06:15 [D|dyn|8842882c] ExecutionPlan 9d547753-5be8-4bbe-a8fb-4ad4cdbcab4a pending >> planning
After that it just stops.
A working one in contrast looks like this:
2023-02-08T17:06:14 [I|app|b7d08e91] Started POST "/api/config_reports" for 10.160.236.27 at 2023-02-08 17:06:14 +0100
2023-02-08T17:06:14 [I|app|b7d08e91] Processing by Api::V2::ConfigReportsController#create as JSON
2023-02-08T17:06:14 [I|app|b7d08e91] Parameters: {"config_report"=>"[FILTERED]", "apiv"=>"v2"}
2023-02-08T17:06:14 [D|app|b7d08e91] Client sent certificate with subject 'puppetproxy.example.com' and subject alt names '["puppetproxy.example.com"]'
2023-02-08T17:06:14 [D|app|b7d08e91] CN and SANs were extracted from a client certificate.
2023-02-08T17:06:14 [D|app|b7d08e91] Verifying request from ["puppetproxy.example.com"] against [<list of smartproxies>]
2023-02-08T17:06:14 [D|app|b7d08e91] Processing report: {"host"=>"client2.example.com", "reported_at"=>"2023-02-08 16:04:55 UTC", "status"=>{"applied"=>0, "restarted"=>0, "failed"=>0, "failed_restarts"=>0, "skipped"=>0, "pending"=>0}, "metrics"=>{"resources"=>{"changed"=>0, "corrective_change"=>0, "failed"=>0, "failed_to_restart"=>0, "out_of_sync"=>0, "restarted"=>0, "scheduled"=>0, "skipped"=>0, "total"=>470}, "time"=>{"anchor"=>0.0006209519999999999, "augeas"=>1.102024248, "catalog_application"=>20.337088896892965, "concat_file"=>0.0005039210000000001, "concat_fragment"=>0.002566903, "config_retrieval"=>9.418634302914143, "convert_catalog"=>0.6509699751622975, "cron"=>0.000336297, "db_directory_structure"=>0.000367473, "exec"=>0.4483568569999998, "fact_generation"=>43.86517295893282, "file"=>4.41000895, "file_line"=>0.009369503999999997, "filebucket"=>5.3675e-05, "filesystem"=>0.10848193199999999, "group"=>0.0027809059999999997, "logical_volume"=>0.652032909, "mount"=>0.009028445999999999, "network_config"=>0.000573699, "network_route"=>0.00043816600000000003, "package"=>11.849279049, "plugin_sync"=>2.670822272077203, "selboolean"=>0.011466918, "selinux_fcontext"=>0.000372647, "service"=>0.34027973599999994, "ssh_authorized_key"=>0.0027460539999999995, "sysctl"=>0.0031915369999999995, "total"=>77.970639304, "transaction_evaluation"=>20.270092835649848, "user"=>0.009942660999999998, "yum_cron_config"=>0.006404968999999999}, "changes"=>{"total"=>0}, "events"=>{"failure"=>0, "success"=>0, "total"=>0}}, "logs"=>[{"log"=>{"sources"=>{"source"=>"Puppet"}, "messages"=>{"message"=>"Applied catalog in 20.34 seconds"}, "level"=>"notice"}}]}
2023-02-08T17:06:14 [I|app|b7d08e91] ForemanWebhooks::EventSubscriber: host_updated.event.foreman event received
2023-02-08T17:06:14 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:14 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:14 [D|dyn|b7d08e91] ExecutionPlan 6af23aee-9bb5-4c2c-8a5f-493cb3a10214 pending >> planning
2023-02-08T17:06:14 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:14 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:14 [D|dyn|b7d08e91] Step 6af23aee-9bb5-4c2c-8a5f-493cb3a10214: 1 pending >> running in phase Plan Dynflow::ActiveJob::QueueAdapters::JobWrapper
2023-02-08T17:06:14 [D|dyn|b7d08e91] Step 6af23aee-9bb5-4c2c-8a5f-493cb3a10214: 1 running >> success in phase Plan Dynflow::ActiveJob::QueueAdapters::JobWrapper
2023-02-08T17:06:14 [D|dyn|b7d08e91] ExecutionPlan 6af23aee-9bb5-4c2c-8a5f-493cb3a10214 planning >> planned
2023-02-08T17:06:14 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:14 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:14 [I|app|b7d08e91] Enqueued ForemanWebhooks::DeliverWebhookJob (Job ID: 6af23aee-9bb5-4c2c-8a5f-493cb3a10214) to Dynflow(default) with arguments: {:event_name=>"host_updated.event.foreman", :payload=>"{\"id\":2865,\"fqdn\":\"client2.example.com\",\"os\":{\"id\":18,\"major\":\"7\",\"name\":\"RedHat\",\"minor\":\"9\",\"nameindicator\":null,\"created_at\":\"2020-10-07T09:03:19.287Z\",\"updated_at\":\"2020-10-13T05:24:48.900Z\",\"release_name\":\"\",\"description\":\"RHEL Server 7.9\",\"password_hash\":\"SHA256\",\"title\":\"RHEL Server 7.9\"},\"hostgroup\":{\"id\":94,\"name\":\"Konsolidierung\",\"created_at\":\"2018-01-10T15:46:03.096Z\",\"updated_at\":\"2018-01-10T15:46:03.096Z\",\"operatingsystem_id\":null,\"architecture_id\":null,\"medium_id\":null,\"ptable_id\":92,\"root_pass\":\"redacted\",\"puppet_ca_proxy_id\":null,\"use_image\":null,\"image_file\":\"\",\"ancestry\":\"1/17/76\",\"vm_defaults\":null,\"subnet_id\":23,\"domain_id\":null,\"puppet_proxy_id\":3,\"title\":\"mia-base/db/oracle/Konsolidierung\",\"realm_id\":null,\"compute_profile_id\":null,\"grub_pass\":\"\",\"lookup_value_matcher\":\"hostgroup=mia-base/db/oracle/Konsolidierung\",\"subnet6_id\":null,\"pxe_loader\":\"PXELinux BIOS\",\"description\":null,\"compute_resource_id\":null,\"content_facet_attributes\":{\"id\":73,\"hostgroup_id\":94,\"kickstart_repository_id\":null,\"content_source_id\":6,\"content_view_id\":8,\"lifecycle_environment_id\":3},\"puppet_attributes\":{\"id\":3,\"hostgroup_id\":94,\"environment_id\":14,\"puppet_proxy_id\":null,\"created_at\":null,\"updated_at\":null}},\"event_name\":\"host_updated.event.foreman\",\"webhook_id\":2,\"context\":{\"remote_ip\":\"10.160.236.27\",\"request\":\"b7d08e91-c149-4873-9636-cac6c2eb24a6\",\"session\":\"b7d08e91-c149-4873-9636-cac6c2eb24a6\",\"user_login\":\"foreman_api_admin\",\"user_admin\":true}}", :headers=>nil, :url=>"https://foreman.example.com:9090/shellhook/cli", :webhook_id=>2}
2023-02-08T17:06:14 [I|app|b7d08e91] Scanning report with: Foreman::PuppetReportScanner
2023-02-08T17:06:14 [D|app|b7d08e91] Changes after reporter specific data added: {"host_id"=>[nil, 2865], "reported_at"=>[nil, Wed, 08 Feb 2023 16:04:55 UTC +00:00], "status"=>[nil, 0], "metrics"=>[nil, "---\nresources: !ruby/hash:ActiveSupport::HashWithIndifferentAccess\n changed: 0\n corrective_change: 0\n failed: 0\n failed_to_restart: 0\n out_of_sync: 0\n restarted: 0\n scheduled: 0\n skipped: 0\n total: 470\ntime: !ruby/hash:ActiveSupport::HashWithIndifferentAccess\n anchor: 0.0006209519999999999\n augeas: 1.102024248\n catalog_application: 20.337088896892965\n concat_file: 0.0005039210000000001\n concat_fragment: 0.002566903\n config_retrieval: 9.418634302914143\n convert_catalog: 0.6509699751622975\n cron: 0.000336297\n db_directory_structure: 0.000367473\n exec: 0.4483568569999998\n fact_generation: 43.86517295893282\n file: 4.41000895\n file_line: 0.009369503999999997\n filebucket: 5.3675e-05\n filesystem: 0.10848193199999999\n group: 0.0027809059999999997\n logical_volume: 0.652032909\n mount: 0.009028445999999999\n network_config: 0.000573699\n network_route: 0.00043816600000000003\n package: 11.849279049\n plugin_sync: 2.670822272077203\n selboolean: 0.011466918\n selinux_fcontext: 0.000372647\n service: 0.34027973599999994\n ssh_authorized_key: 0.0027460539999999995\n sysctl: 0.0031915369999999995\n total: 77.970639304\n transaction_evaluation: 20.270092835649848\n user: 0.009942660999999998\n yum_cron_config: 0.006404968999999999\nchanges: !ruby/hash:ActiveSupport::HashWithIndifferentAccess\n total: 0\nevents: !ruby/hash:ActiveSupport::HashWithIndifferentAccess\n failure: 0\n success: 0\n total: 0\n"], "origin"=>[nil, "Puppet"]}
2023-02-08T17:06:14 [I|app|b7d08e91] ForemanWebhooks::EventSubscriber: host_updated.event.foreman event received
2023-02-08T17:06:14 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:14 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:14 [D|dyn|b7d08e91] ExecutionPlan 5d9e5419-b685-4ed3-900a-a28bb25dfb58 pending >> planning
2023-02-08T17:06:14 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:14 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:14 [D|dyn|b7d08e91] Step 5d9e5419-b685-4ed3-900a-a28bb25dfb58: 1 pending >> running in phase Plan Dynflow::ActiveJob::QueueAdapters::JobWrapper
2023-02-08T17:06:15 [D|dyn|b7d08e91] Step 5d9e5419-b685-4ed3-900a-a28bb25dfb58: 1 running >> success in phase Plan Dynflow::ActiveJob::QueueAdapters::JobWrapper
2023-02-08T17:06:15 [D|dyn|b7d08e91] ExecutionPlan 5d9e5419-b685-4ed3-900a-a28bb25dfb58 planning >> planned
2023-02-08T17:06:15 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:15 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:15 [I|app|b7d08e91] Enqueued ForemanWebhooks::DeliverWebhookJob (Job ID: 5d9e5419-b685-4ed3-900a-a28bb25dfb58) to Dynflow(default) with arguments: {:event_name=>"host_updated.event.foreman", :payload=>"{\"id\":2865,\"fqdn\":\"client2.example.com\",\"os\":{\"id\":18,\"major\":\"7\",\"name\":\"RedHat\",\"minor\":\"9\",\"nameindicator\":null,\"created_at\":\"2020-10-07T09:03:19.287Z\",\"updated_at\":\"2020-10-13T05:24:48.900Z\",\"release_name\":\"\",\"description\":\"RHEL Server 7.9\",\"password_hash\":\"SHA256\",\"title\":\"RHEL Server 7.9\"},\"hostgroup\":{\"id\":94,\"name\":\"Konsolidierung\",\"created_at\":\"2018-01-10T15:46:03.096Z\",\"updated_at\":\"2018-01-10T15:46:03.096Z\",\"operatingsystem_id\":null,\"architecture_id\":null,\"medium_id\":null,\"ptable_id\":92,\"root_pass\":\"$5$nK3JpWJe$kZzjsK5p5/m1eddqPb0I.cKGniajzAth9B81AmxgtqB\",\"puppet_ca_proxy_id\":null,\"use_image\":null,\"image_file\":\"\",\"ancestry\":\"1/17/76\",\"vm_defaults\":null,\"subnet_id\":23,\"domain_id\":null,\"puppet_proxy_id\":3,\"title\":\"mia-base/db/oracle/Konsolidierung\",\"realm_id\":null,\"compute_profile_id\":null,\"grub_pass\":\"\",\"lookup_value_matcher\":\"hostgroup=mia-base/db/oracle/Konsolidierung\",\"subnet6_id\":null,\"pxe_loader\":\"PXELinux BIOS\",\"description\":null,\"compute_resource_id\":null,\"content_facet_attributes\":{\"id\":73,\"hostgroup_id\":94,\"kickstart_repository_id\":null,\"content_source_id\":6,\"content_view_id\":8,\"lifecycle_environment_id\":3},\"puppet_attributes\":{\"id\":3,\"hostgroup_id\":94,\"environment_id\":14,\"puppet_proxy_id\":null,\"created_at\":null,\"updated_at\":null}},\"event_name\":\"host_updated.event.foreman\",\"webhook_id\":2,\"context\":{\"request\":\"b7d08e91-c149-4873-9636-cac6c2eb24a6\",\"user_login\":\"foreman_api_admin\",\"user_admin\":true}}", :headers=>nil, :url=>"https://foreman.example.com:9090/shellhook/cli", :webhook_id=>2}
2023-02-08T17:06:15 [I|app|b7d08e91] ForemanWebhooks::EventSubscriber: host_updated.event.foreman event received
2023-02-08T17:06:15 [I|app|b7d08e91] Performing ForemanWebhooks::DeliverWebhookJob (Job ID: 6af23aee-9bb5-4c2c-8a5f-493cb3a10214) from Dynflow(default) enqueued at 2023-02-08T16:06:14Z with arguments: {:event_name=>"host_updated.event.foreman", :payload=>#<Sequel::SQL::Blob:0x36ee8 bytes=1529 start="{\"id\":2865" end="in\":true}}">, :headers=>nil, :url=>"https://foreman.example.com:9090/shellhook/cli", :webhook_id=>2}
2023-02-08T17:06:15 [I|app|b7d08e91] Performing 'Host Updated' webhook request for event 'host_updated.event.foreman'
2023-02-08T17:06:15 [W|app|b7d08e91] Could not parse HTTP headers JSON, ignoring: no implicit conversion of nil into String
2023-02-08T17:06:15 [D|app|b7d08e91] Headers:
2023-02-08T17:06:15 [D|app|b7d08e91] Webhook POST request: https://foreman.example.com:9090/shellhook/cli
2023-02-08T17:06:15 [D|app|b7d08e91] Headers: {"accept-encoding"=>["gzip;q=1.0,deflate;q=0.6,identity;q=0.3"], "accept"=>["*/*"], "user-agent"=>["Ruby"], "content-type"=>["plain/text"], "x-request-id"=>["b7d08e91-c149-4873-9636-cac6c2eb24a6"], "x-session-id"=>["6a151b18-8de0-4d36-bf21-6a1c5ace888c"]}
2023-02-08T17:06:15 [D|app|b7d08e91] Body: #<Sequel::SQL::Blob:0x36ee8 bytes=1529 start="{\"id\":2865" end="in\":true}}">
2023-02-08T17:06:15 [I|app|b7d08e91] POST response was 200
2023-02-08T17:06:15 [I|app|b7d08e91] Performed ForemanWebhooks::DeliverWebhookJob (Job ID: 6af23aee-9bb5-4c2c-8a5f-493cb3a10214) from Dynflow(default) in 18.07ms
2023-02-08T17:06:15 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:15 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:15 [D|dyn|b7d08e91] Step 6af23aee-9bb5-4c2c-8a5f-493cb3a10214: 2 running >> success in phase Run Dynflow::ActiveJob::QueueAdapters::JobWrapper
2023-02-08T17:06:15 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:15 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:15 [D|dyn|b7d08e91] ExecutionPlan 332dd2ea-e898-4d6e-a96c-293e418ff39c pending >> planning
2023-02-08T17:06:15 [I|app|b7d08e91] Performing ForemanWebhooks::DeliverWebhookJob (Job ID: 5d9e5419-b685-4ed3-900a-a28bb25dfb58) from Dynflow(default) enqueued at 2023-02-08T16:06:14Z with arguments: {:event_name=>"host_updated.event.foreman", :payload=>#<Sequel::SQL::Blob:0x37078 bytes=1452 start="{\"id\":2865" end="in\":true}}">, :headers=>nil, :url=>"https://foreman.example.com:9090/shellhook/cli", :webhook_id=>2}
2023-02-08T17:06:15 [I|app|b7d08e91] Performing 'Host Updated' webhook request for event 'host_updated.event.foreman'
2023-02-08T17:06:15 [W|app|b7d08e91] Could not parse HTTP headers JSON, ignoring: no implicit conversion of nil into String
2023-02-08T17:06:15 [D|app|b7d08e91] Headers:
2023-02-08T17:06:15 [D|app|b7d08e91] Webhook POST request: https://foreman.example.com:9090/shellhook/cli
2023-02-08T17:06:15 [D|app|b7d08e91] Headers: {"accept-encoding"=>["gzip;q=1.0,deflate;q=0.6,identity;q=0.3"], "accept"=>["*/*"], "user-agent"=>["Ruby"], "content-type"=>["plain/text"], "x-request-id"=>["b7d08e91-c149-4873-9636-cac6c2eb24a6"], "x-session-id"=>["9d874e63-1969-4b3f-828b-f440c6bcd428"]}
2023-02-08T17:06:15 [D|app|b7d08e91] Body: #<Sequel::SQL::Blob:0x37078 bytes=1452 start="{\"id\":2865" end="in\":true}}">
2023-02-08T17:06:15 [I|app|b7d08e91] POST response was 200
2023-02-08T17:06:15 [I|app|b7d08e91] Performed ForemanWebhooks::DeliverWebhookJob (Job ID: 5d9e5419-b685-4ed3-900a-a28bb25dfb58) from Dynflow(default) in 10.65ms
2023-02-08T17:06:15 [D|tax|b7d08e91] Current organization set to none
2023-02-08T17:06:15 [D|tax|b7d08e91] Current location set to none
2023-02-08T17:06:15 [D|dyn|b7d08e91] Step 5d9e5419-b685-4ed3-900a-a28bb25dfb58: 2 running >> success in phase Run Dynflow::ActiveJob::QueueAdapters::JobWrapper
If you want me to look for anything else in particular, please tell me what I should look for or how I can drop that file directly to someone to take a look at it. The raw text of about 1 minute of running in debug mode is already 4.5 MB, and I don’t see me anonymizing everything in there so I can post it publicly.
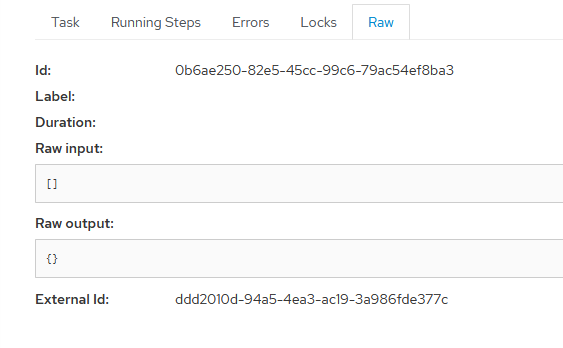


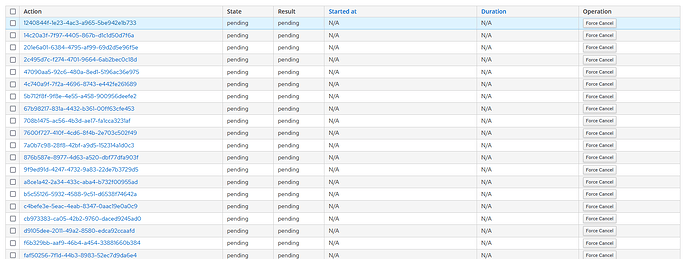
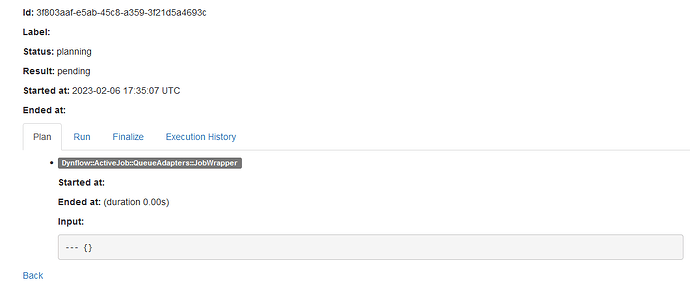
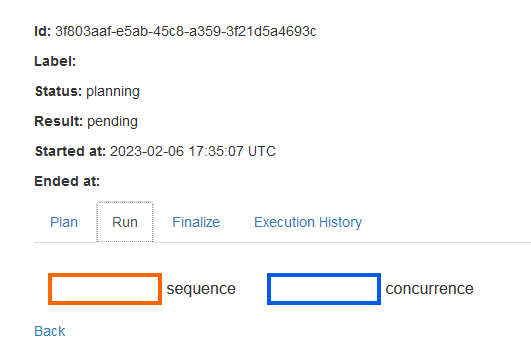
 Could you show us what dynflow console shows for those tasks? There should be a button for it somewhere (or just go to $foreman/foreman_tasks/dynflow/$external_id ?
Could you show us what dynflow console shows for those tasks? There should be a button for it somewhere (or just go to $foreman/foreman_tasks/dynflow/$external_id ?