Ohai!
I would like to propose (well, really, repeat a proposal that we heard in the past) to give plugin maintainers the permission to merge packaging changes to their respective plugins.
Who, if not the maintainers, know best what changes need to happen to the package of a plugin?
Also, there is not really an extension of permissions – of people wanted to do something malicious, they already could do so by doing a malicious release that gets packaged.
As a practical example, this would mean that we’d give the @theforeman/remote-execution team the permission to merge PRs in rpm/develop if they only touch files in:
plugins/rubygem-foreman_remote_execution/plugins/rubygem-smart_proxy_remote_execution_ssh/plugins/rubygem-hammer_cli_foreman_remote_execution/
Implementation
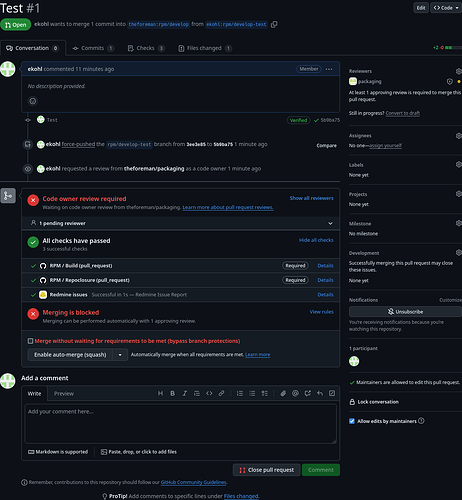
The idea is to implement this using branch protection rules and CODEOWNERS.
We can configure GitHub to only allow pushes to rpm/develop (and others) if there is a PR and that PR is approved by a code owner.
Then we configure the CODEOWNERS file to read something like this:
* @theforeman/packaging
/packages/plugins/*remote_execution*/ @theforeman/packaging @theforeman/remote-execution
Which means that things that match *remote_execution* are owned by packaging and rex teams, the rest only by packaging.
We can now give @theforeman/remote-execution merge permissions to the whole repository (as you can’t give per-path permissions) and the branch protection will still disallow merges to things outside REX packages.
As a side-effect, this will also generate notifications to the REX team whenever someone (or something, like our automation) opens a PR to one of their packages.
Open Questions
Do we want this?
While my assumption is yes, I still want to hear if someone is against this proposal ![]()
Do we implement that for all teams, or opt-in?
Giving teams/people merge rights and adding them as code owners will subscribe them to changes in this repo and also generate notifications when a review a requested.
If we implement that for all plugins in one go, this can create quite some notification load on the humans involved. The alternative would be to start with an “empty” set and add people/teams as they think it makes sense for them.