Problem:
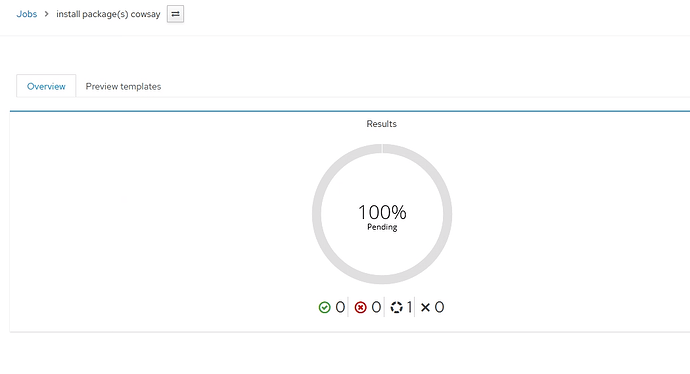
Remote execution doesn’t use ssh key and passphrase to login to target host and just gets stuck waiting.
/var/log/secure
May 4 13:10:30 foreman sshd[1015232]: Postponed publickey for foreman-remote from 123.123.123.123 port 34308 ssh2 [preauth]
So according to that remote execution is not even attempting to use the ssh key.
Config
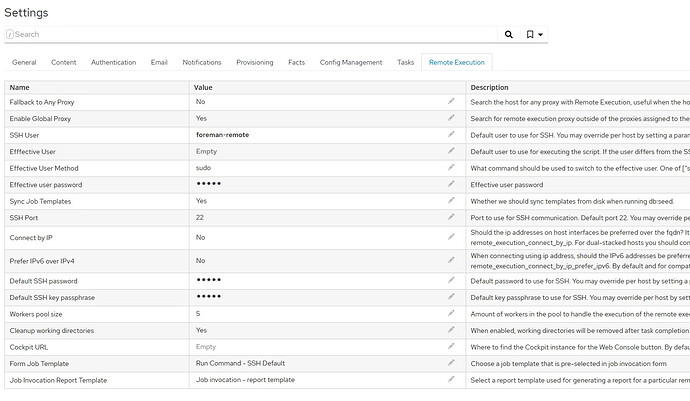
cat /etc/foreman-proxy/settings.d/remote_execution_ssh.yml
---
:enabled: https
:ssh_identity_key_file: /var/lib/foreman-proxy/ssh/id_ecdsa
:local_working_dir: /var/tmp
:remote_working_dir: /var/tmp
:kerberos_auth: false
# Whether to run remote execution jobs asynchronously
:mode: ssh
#############################
Manual attempt with a key works. And also informs of failed logins so it has atleast attemped some ssh connection. But seeing the
ssh -i /var/lib/foreman-proxy/ssh/id_ecdsa foreman-remote@foreman.example.com
Enter passphrase for key '/var/lib/foreman-proxy/ssh/id_ecdsa':
UNAUTHORIZED ACCESS TO THIS DEVICE IS PROHIBITED
All activities performed on this device are logged and monitored.
Last failed login: Wed May 4 03:22:05 EEST 2022 from foreman.example.com on ssh:notty
There were 7 failed login attempts since the last successful login.
Last login: Tue May 3 15:41:47 2022 from foreman.example.com
/var/log/secure on manual attempt
May 4 11:03:57 foreman sshd[1008201]: Accepted publickey for foreman-remote from 123.123.123.123 port 57884 ssh2:
May 4 11:03:57 foreman systemd[1008217]: pam_unix(systemd-user:session): session opened for user foreman-remote by (uid=0)
May 4 11:03:57 foreman sshd[1008201]: pam_unix(sshd:session): session opened for user foreman-remote by (uid=0)
Production log on the task.
2022-05-04T13:10:29 [I|app|d2d9732f] Parameters: {"utf8"=>"✓", "authenticity_token"=>"1/hdSyv7VN65n4r8ZNML+Tg9sEBomtn2FoYLc/IdmQ3JTecvdQov6FHJo4Fq1i7oDouKmm0duZmkJF31oG5WVw==", "job_invocation"=>{"job_category"=>"Packages", "remote_execution_feature_id"=>"", "providers"=>{"SSH"=>{"job_template_id"=>"143", "job_tem
plates"=>{"141"=>{"effective_user"=>"", "execution_timeout_interval"=>""}, "143"=>{"input_values"=>"[FILTERED]", "effective_user"=>"", "execution_timeout_interval"=>""}}}}, "description"=>"", "description_override"=>"%{action} package(s) %{package}", "description_format"=>"%{action} package(s) %{package}", "password
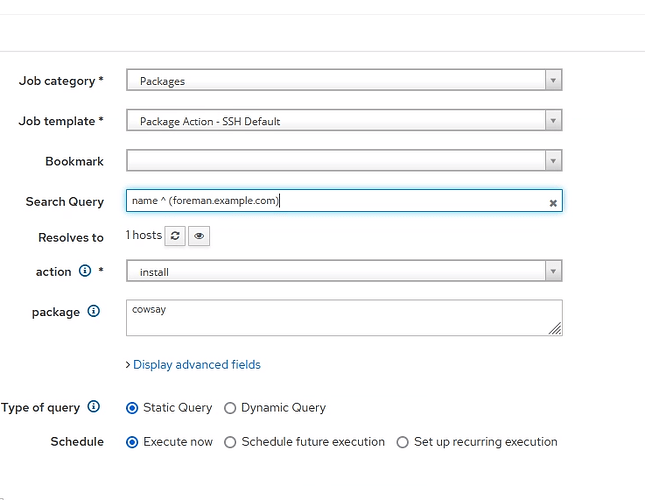
"=>"[FILTERED]", "key_passphrase"=>"redacted_since_this_was_plaintext", "effective_user_password"=>"[FILTERED]", "concurrency_level"=>"", "time_span"=>""}, "targeting"=>{"bookmark_id"=>"", "search_query"=>"name ^ (foreman.palvelu.local)", "randomized_ordering"=>"false", "targeting_type"=>"static_query"}, "fakepassword"=>"[FILTER
ED]", "triggering"=>{"mode"=>"immediate", "start_at_raw"=>"2022-05-04 13:10", "start_before_raw"=>"", "input_type"=>"daily", "cronline"=>"", "days"=>"", "days_of_week"=>{"1"=>"0", "2"=>"0", "3"=>"0", "4"=>"0", "5"=>"0", "6"=>"0", "7"=>"0"}, "time"=>{"time(1i)"=>"2022", "time(2i)"=>"5", "time(3i)"=>"4", "time(4i)"=>"
13", "time(5i)"=>"10"}, "max_iteration"=>"", "end_time_limited"=>"false", "end_time"=>{"end_time(1i)"=>"2022", "end_time(2i)"=>"5", "end_time(3i)"=>"4", "end_time(4i)"=>"13", "end_time(5i)"=>"10"}, "purpose"=>""}, "commit"=>"Submit"}
Expected outcome:
Remote execution uses ssh key and passphrase and
Foreman and Proxy versions:
foreman 3.2.0
| foreman-tasks | The goal of this plugin is to unify the way of showing task statuses across the Foreman instance. It defines Task model for keeping the information about the tasks and Lock for assigning the tasks to resources. The locking allows dealing with preventing multiple colliding tasks to be run on the same resource. It also optionally provides Dynflow infrastructure for using it for managing the tasks. | Ivan Nečas | 6.0.1 |
|---|---|---|---|
| foreman_puppet | Allow assigning Puppet environments and classes to the Foreman Hosts. | Ondřej Ezr and Shira Maximov | 3.0.5 |
| foreman_remote_execution | A plugin bringing remote execution to the Foreman, completing the config management functionality with remote management functionality. | Foreman Remote Execution team | 6.0.0 |
| katello | Katello adds Content and Subscription Management to Foreman. For this it relies on Candlepin and Pulp. | N/A | 4.4.0.2 |
candlepin-4.1.10-1.el8.noarch
candlepin-selinux-4.1.10-1.el8.noarch
foreman-3.2.0-1.el8.noarch
foreman-cli-3.2.0-1.el8.noarch
foreman-debug-3.2.0-1.el8.noarch
foreman-dynflow-sidekiq-3.2.0-1.el8.noarch
foreman-installer-3.2.0-1.el8.noarch
foreman-installer-katello-3.2.0-1.el8.noarch
foreman-postgresql-3.2.0-1.el8.noarch
foreman-proxy-3.2.0-1.el8.noarch
foreman-release-3.2.0-1.el8.noarch
foreman-selinux-3.2.0-1.el8.noarch
foreman-service-3.2.0-1.el8.noarch
foreman.palvelu.local-apache-1.0-2.noarch
foreman.palvelu.local-foreman-client-1.0-1.noarch
foreman.palvelu.local-foreman-proxy-1.0-2.noarch
foreman.palvelu.local-foreman-proxy-client-1.0-1.noarch
foreman.palvelu.local-puppet-client-1.0-1.noarch
katello-4.4.0-1.el8.noarch
katello-ca-consumer-foreman.palvelu.local-1.0-2.noarch
katello-certs-tools-2.8.2-1.el8.noarch
katello-client-bootstrap-1.7.8-1.el8.noarch
katello-common-4.4.0-1.el8.noarch
katello-debug-4.4.0-1.el8.noarch
katello-default-ca-1.0-1.noarch
katello-repos-4.4.0-1.el8.noarch
katello-selinux-4.0.2-1.el8.noarch
katello-server-ca-1.0-2.noarch
pulp-client-1.0-1.noarch
pulpcore-selinux-1.3.0-1.el8.x86_64
python38-pulp-ansible-0.10.1-1.el8.noarch
python38-pulp-certguard-1.5.1-1.el8.noarch
python38-pulp-container-2.9.2-1.el8.noarch
python38-pulp-deb-2.16.1-1.el8.noarch
python38-pulp-file-1.10.1-1.el8.noarch
python38-pulp-python-3.5.2-1.el8.noarch
python38-pulp-rpm-3.17.3-2.el8.noarch
python38-pulpcore-3.16.7-1.el8.noarch
qpid-proton-c-0.35.0-1.el8.x86_64
rubygem-foreman-tasks-6.0.1-1.fm3_2.el8.noarch
rubygem-foreman_maintain-1.0.3-1.el8.noarch
rubygem-foreman_puppet-3.0.5-1.fm3_2.el8.noarch
rubygem-foreman_remote_execution-6.0.0-1.fm3_2.el8.noarch
rubygem-hammer_cli-3.2.0-1.20220214173651git27087bf.el8.noarch
rubygem-hammer_cli_foreman-3.2.0-1.20220214175116git323f240.el8.noarch
rubygem-hammer_cli_foreman_puppet-0.0.4-1.fm3_1.el8.noarch
rubygem-hammer_cli_foreman_remote_execution-0.2.2-1.fm3_0.el8.noarch
rubygem-hammer_cli_foreman_tasks-0.0.17-1.fm3_2.el8.noarch
rubygem-hammer_cli_katello-1.4.1-1.el8.noarch
rubygem-katello-4.4.0.2-2.el8.noarch
rubygem-pulp_ansible_client-0.10.1-1.el8.noarch
rubygem-pulp_certguard_client-1.5.0-1.el8.noarch
rubygem-pulp_container_client-2.9.0-1.el8.noarch
rubygem-pulp_deb_client-2.16.0-1.el8.noarch
rubygem-pulp_file_client-1.10.0-1.el8.noarch
rubygem-pulp_ostree_client-2.0.0-0.1.a1.el8.noarch
rubygem-pulp_python_client-3.5.2-1.el8.noarch
rubygem-pulp_rpm_client-3.17.4-1.el8.noarch
rubygem-pulpcore_client-3.16.0-1.el8.noarch
rubygem-qpid_proton-0.35.0-1.el8.x86_64
rubygem-smart_proxy_pulp-3.2.0-2.fm3_2.el8.noarch
Other relevant data:
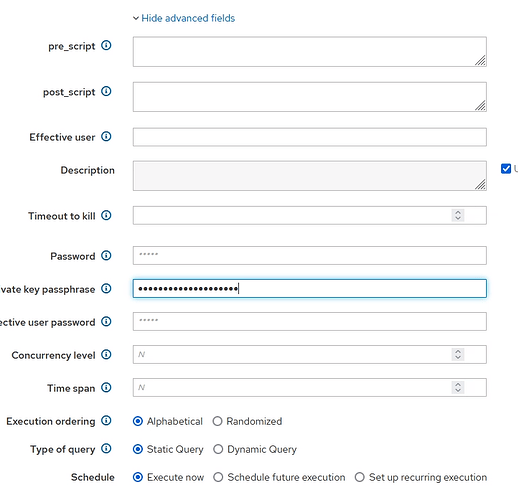
I set the passphrase from the ui and did not set ssh password from there as it was not goint to be used anyway.