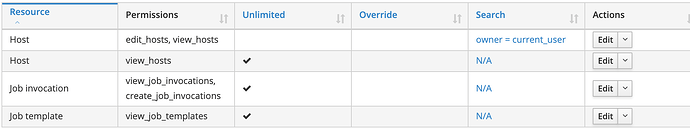
Hello,
today we noticed that the RemoteExecution plugin/feature seems to allow the execution of jobs on all hosts a given user can see in Foreman (given the user has the permission Job invocation/create_job_invocations).
Additionally, the filter of the permission does not allow to limit the rights to a group of hosts based on the Foreman Owner.
Now, image a scenario where we have a usergroup which should be allowed to view and manage their own hosts and also view some additional hosts. If we want to enable Remote Execution for this usergroup, they currently gain REX permissions on all hosts they see.:
Did I miss something or is this the current behaviour?
I would suggest that we implement a new search filter for create_job_invocations to limit the permissions based on the host owner (like host_owner = current_user) or maybe use the edit_host permission instead of view_host.
Manuel
Hi,
in order to be able to execute a job the user has to be able to
a) view the host (view_hosts permission)
b) view the job template they are trying to run (view_job_templates)
c) create template invocations (ie. run given template on a given host, create_template_invocations permission)
d) have some misc permissions related to job invocations
From what I see I’d say you are not putting any limitation on c). By adding filters on that permission (you can search on host.name, host_group.name and job category and name of the template in question) you should be able to put the constraints you want into place.
Note that the user will still be able to trigger a job but it will fail early for hosts where the user doesn’t have the required permissions.
Hi,
the screenshot was taken of a role I created to demonstrate my point - I forgot to add the create_template_invocation permission there. Our active roles do indeed contain that permission - but without any search filter.
However, most of our VMs are not contained in a host group. So limiting on that attribute is sadly not enough. As we have over 2000 VMs, filtering based on the name is also not really practical.
WDYT about a new filter for create_template_invocations (if this is where filtering is done currently) named host_owner?
It sounds like a reasonable request. Could you plase file an RFE in our issue tracker?
1 Like