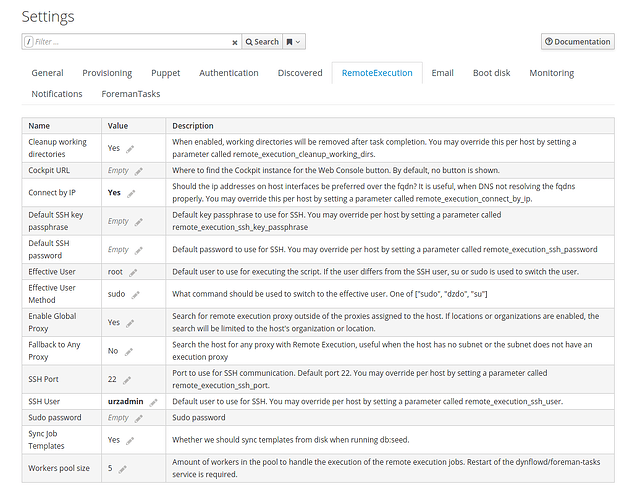
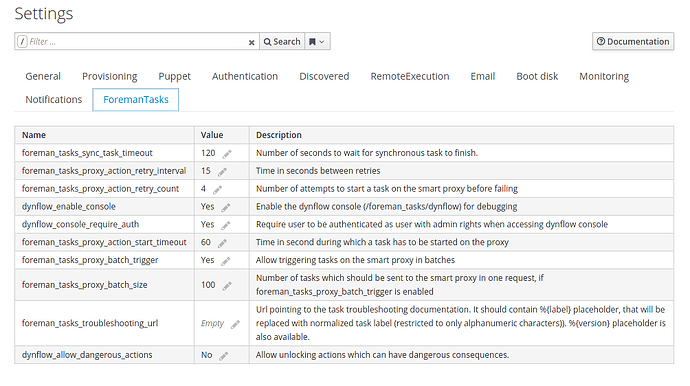
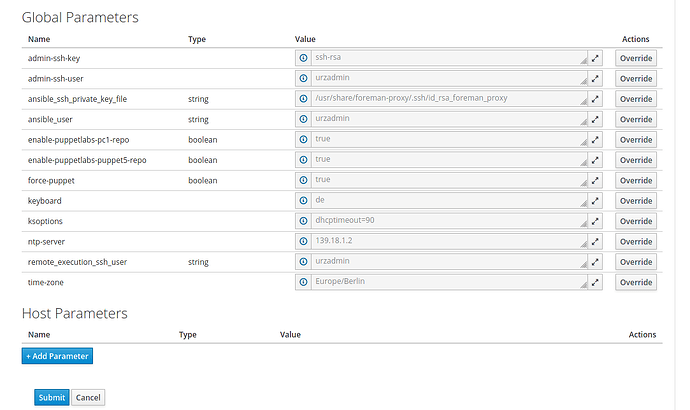
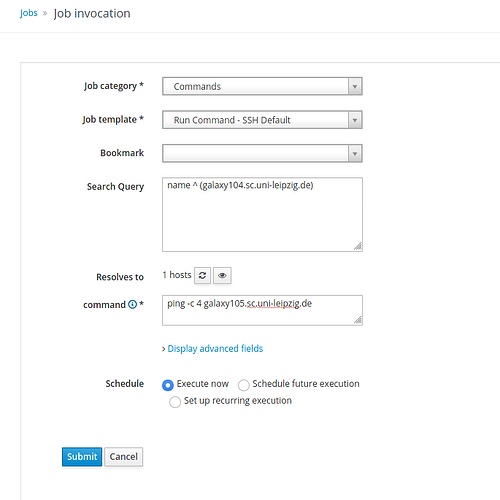
Good morning foremans,
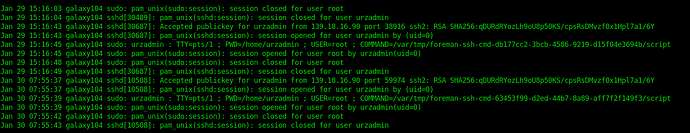
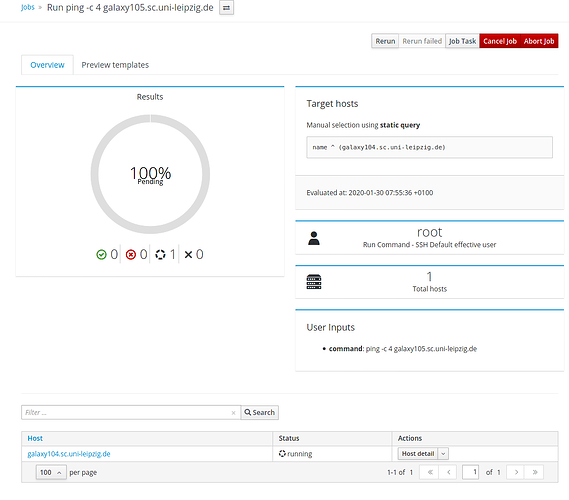
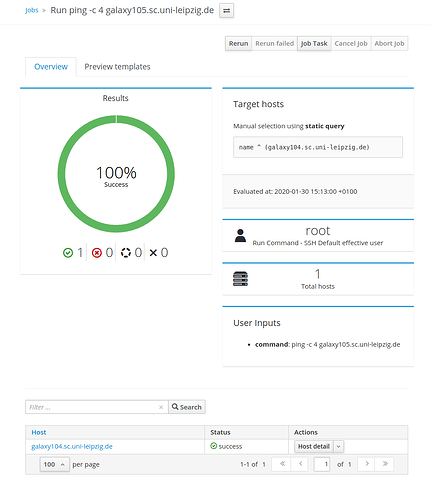
I’m iterating my Foreman installation since 2016 and i tried a few times to use remote exec and Ansible but haven’t been able. The websocket is running with official ssl certificates and somehow i get now feedback from the remote exec task which is definitely running on the remote machine.
Problem:
No feedback of Remote Execution Task from remote host, UI doesn’t get feedback
Expected outcome:
Remote Execution Task ends successful and Foreman UI gets feedback changes status to successful ended
Foreman and Proxy versions:
Foreman 1.23.1 installed using rpms
foreman_remote_execution 1.8.2
Distribution and version:
CentOS Linux release 7.7.1908 (Core)
Other relevant data:
/etc/smart_proxy_dynflow_core/settings.yml:
—
# Path to dynflow database, leave blank for in-memory non-persistent database
:database:
# URL of the foreman, used for reporting back
:foreman_url: 'https://urzlxdeploy.rz.uni-leipzig.de:443'
# SSL settings for client authentication against Foreman
# :foreman_ssl_ca: ssl/foreman_ca.pem
:foreman_ssl_ca: /etc/puppetlabs/puppet/ssl/certs/ca.pem
# :foreman_ssl_key: ssl/foreman_key.pem
:foreman_ssl_key: /etc/pki/tls/private/urzlxdeploy.rz.uni-leipzig.de-pkey-nopw.pem
# :foreman_ssl_cert: ssl/foreman_cert.pem
:foreman_ssl_cert: /etc/ssl/certs/cert-10263428829321932413835964919.pem
:console_auth: false
# Set to true to make the core fork to background after start
# :daemo nize: false
# :pid_file: /var/run/foreman-proxy/smart_proxy_dynflow_core.pid
# Listen on address
:listen: 127.0.0.1
# Listen on port
:port: 8008
# SSL settings for running core as https service
# :use_https: false
# :ssl_ca_file: ssl/ca.pem
# :ssl_private_key: ssl/localhost.pem
# :ssl_certificate: ssl/certs/localhost.pem
# Use this option only if you need to disable certain cipher suites.
# Note: we use the OpenSSL suite name, take a look at:
# https://www.openssl.org/docs/manmaster/apps/ciphers.html#CIPHER-SUITE-NAMES
# for more information.
#:ssl_disabled_ciphers: [CIPHER-SUITE-1, CIPHER-SUITE-2]
# Use this option only if you need to strictly specify TLS versions to be
# disabled. SSLv3 and TLS v1.0 are always disabled and cannot be configured.
# Specify versions like: '1.1', or '1.2'
#:tls_disabled_versions: []
# File to log to, leave empty for logging to STDOUT
:log_file: /var/log/foreman-proxy/smart_proxy_dynflow_core.log
# Log level, one of UNKNOWN, FATAL, ERROR, WARN, INFO, DEBUG
:log_level: WARN
# Maximum age of execution plans to keep before having them cleaned
# by the execution plan cleaner (in seconds), defaults to 24 hours
# :execution_plan_cleaner_age: 86400
/etc/foreman-proxy/settings.d/remote_execution_ssh.yml:
---
:enabled: true
:ssh_identity_key_file: '~/.ssh/id_rsa_foreman_proxy'
:local_working_dir: '/var/tmp'
:remote_working_dir: '/var/tmp'
# :kerberos_auth: false
# :async_ssh: false
# Defines how often (in seconds) should the runner check
# for new data leave empty to use the runner's default
# (1 second for regular, 60 seconds with async_ssh enabled)
# :runner_refresh_interval:
# Defines the verbosity of logging coming from Net::SSH
# one of :debug, :info, :warn, :error, :fatal
# must be lower than general log level
# :ssh_log_level: fatal
/etc/foreman/settings.yaml:
---
### File managed with puppet ###
## Module: 'foreman'
:unattended: true
:login: true
:require_ssl: true
:locations_enabled: false
:organizations_enabled: false
:puppetrun: false
:puppetssldir: /etc/puppetlabs/puppet/ssl
# The following values are used for providing default settings during db migrate
:oauth_active: true
:oauth_map_users: false
:oauth_consumer_key: *
:oauth_consumer_secret: *
# Websockets
:websockets_encrypt: on
#:websockets_ssl_key: /etc/puppetlabs/puppet/ssl/private_keys/urzlxdeploy.rz.uni-leipzig.de.pem
:websockets_ssl_key: /etc/pki/tls/private/urzlxdeploy.rz.uni-leipzig.de-pkey-nopw.pem
#:websockets_ssl_cert: /etc/puppetlabs/puppet/ssl/certs/urzlxdeploy.rz.uni-leipzig.de.pem
:websockets_ssl_cert: /etc/ssl/certs/cert-10263428829321932413835964919.pem
# SSL-settings
:ssl_certificate: /etc/puppetlabs/puppet/ssl/certs/urzlxdeploy.rz.uni-leipzig.de.pem
:ssl_ca_file: /etc/puppetlabs/puppet/ssl/certs/ca.pem
:ssl_priv_key: /etc/puppetlabs/puppet/ssl/private_keys/urzlxdeploy.rz.uni-leipzig.de.pem
# Log settings for the current environment can be adjusted by adding them
# here. For example, if you want to increase the log level.
:logging:
:level: error
# Individual logging types can be toggled on/off here
:loggers:
/etc/httpd/conf.d/05-foreman-ssl.conf:
# ************************************
# Vhost template in module puppetlabs-apache
# Managed by Puppet
# ************************************
<VirtualHost *:443>
ServerName urzlxdeploy.rz.uni-leipzig.de
## Vhost docroot
DocumentRoot "/usr/share/foreman/public"
## Directories, there should at least be a declaration for /usr/share/foreman/public
<Directory "/usr/share/foreman/public">
Options SymLinksIfOwnerMatch
AllowOverride None
Require all granted
</Directory>
## Logging
ErrorLog "/var/log/httpd/foreman-ssl_error_ssl.log"
ServerSignature Off
CustomLog "/var/log/httpd/foreman-ssl_access_ssl.log" combined
## Server aliases
ServerAlias foreman
## SSL directives
SSLEngine on
#SSLCertificateFile "/etc/puppetlabs/puppet/ssl/certs/urzlxdeploy.rz.uni-leipzig.de.pem"
SSLCertificateFile "/etc/ssl/certs/cert-10263428829321932413835964919.pem"
#SSLCertificateKeyFile "/etc/puppetlabs/puppet/ssl/private_keys/urzlxdeploy.rz.uni-leipzig.de.pem"
SSLCertificateKeyFile "/etc/pki/tls/private/urzlxdeploy.rz.uni-leipzig.de-pkey-nopw.pem"
SSLCertificateChainFile "/etc/ssl/certs/cachain.crt"
SSLVerifyClient optional
SSLCACertificateFile "/etc/puppetlabs/puppet/ssl/certs/ca.pem"
SSLCARevocationFile "/etc/puppetlabs/puppet/ssl/crl.pem"
SSLVerifyDepth 3
SSLCARevocationCheck "chain"
SSLOptions +StdEnvVars +ExportCertData
## Custom fragment [20/1680]
# Static public dir serving
<Directory /usr/share/foreman/public>
<IfVersion < 2.4>
Allow from all
</IfVersion>
<IfVersion >= 2.4>
Require all granted
</IfVersion>
</Directory>
<Directory ~ /usr/share/foreman/public/(assets|webpack)>
# Use standard http expire header for assets instead of ETag
<IfModule mod_expires.c>
Header unset ETag
FileETag None
ExpiresActive On
ExpiresDefault "access plus 1 year"
</IfModule>
# Return compressed assets if they are precompiled
<IfModule mod_rewrite.c>
RewriteEngine on
# Make sure the browser supports gzip encoding and file with .gz added
# does exist on disc before we rewrite with the extension
RewriteCond %{HTTP:Accept-Encoding} \b(x-)?gzip\b
RewriteCond %{REQUEST_FILENAME} \.(css|js|svg)$
RewriteCond %{REQUEST_FILENAME}.gz -s
RewriteRule ^(.+) $1.gz [L]
# Set headers for all possible assets which are compressed
<FilesMatch \.css\.gz$>
ForceType text/css
Header set Content-Encoding gzip
SetEnv no-gzip
</FilesMatch>
<FilesMatch \.js\.gz$>
ForceType text/javascript
Header set Content-Encoding gzip
SetEnv no-gzip
</FilesMatch>
<FilesMatch \.svg\.gz$>
ForceType image/svg+xml
Header set Content-Encoding gzip
SetEnv no-gzip
</FilesMatch>
</IfModule>
</Directory>
<IfVersion < 2.4>
Include /etc/httpd/conf.d/05-foreman-ssl.d/*.conf
</IfVersion>
<IfVersion >= 2.4>
IncludeOptional /etc/httpd/conf.d/05-foreman-ssl.d/*.conf
</IfVersion>
PassengerAppRoot /usr/share/foreman
PassengerRuby /usr/bin/tfm-ruby
PassengerMinInstances 1
PassengerStartTimeout 600
PassengerPreStart https://urzlxdeploy.rz.uni-leipzig.de:443
AddDefaultCharset UTF-8
KeepAlive on
KeepAliveTimeout 5
MaxKeepAliveRequests 100
</VirtualHost>
Thanks in advance,
Vadim