Hey so i think i got a pretty major problem, the cert for puppet seems to have expired last week and now foreman and puppet will no longer run on any workstation.
Using the proceedure here: Renewing CA certificates procedure I attempted to renew the puppetCA cert. It did seem to work, but did not fix my clients. I restarted the foreman server and then i could not log in to the backend of foreman (webpage), so had to revert to snapshot. However the webserver certificate had been updated (new expiry 2033), so i think i was successful regenerating the certs. However like i said, my username and pass no longer worked on the backend and so i had to revert. Not sure why that happened…
Anyone got some more complete instructions? because i assume i am missing something. I basically followed this guide ( Renew/Extend Puppet CA/puppetmasterd certs | Arrfab's blog ) substituting /etc/puppetlabs/puppet/ssl/ with the path they were using
client error is:
If anyone knows a client config that will just bypass certificates in general that would be a solid work around too. I just need this to work. I have a feeling i am pretty stuck as I wont have any way to distribute any change to the clients (or i have to come up with a way like group policy…)
Foreman version is 3.1.2
here is the instructions i was drafting, everything i did so far to try and fix this. Hopefully i am just missing one small step and its not as bad as i think it is ![]()
1.) back up old certificates just incase (can do snapshot as well in vmware)
tar cvzf /root/puppet-ssl-backup.2023.03.28.gz /etc/puppetlabs/puppet/ssl/
2.) Check that the ca_key.pem and existing ca_crt.pem match
cd /etc/puppetlabs/puppet/ssl/ca
( openssl rsa -noout -modulus -in ca_key.pem 2> /dev/null | openssl md5 ; openssl x509 -noout -modulus -in ca_crt.pem 2> /dev/null | openssl md5 )3.) Generate a new CSR.
openssl x509 -x509toreq -in ca_crt.pem -signkey ca_key.pem -out ca_csr.pem
4.) sign the CSR for the CA
cat > extension.cnf << EOF
[CA_extensions]
basicConstraints = critical,CA:TRUE
nsComment = “Puppet Foreman Internal Certificate”
keyUsage = critical,keyCertSign,cRLSign
subjectKeyIdentifier = hash
EOF5.) And now archive old CA crt and sign (new) extended one.
cp ca_crt.pem ca_crt.pem.old
openssl x509 -req -days 3650 -in ca_csr.pem -signkey ca_key.pem -out ca_crt.pem -extfile extension.cnf -extensions CA_extensions
6.) check the cert
openssl x509 -in ca_crt.pem -noout -text|grep -A 3 Validity
7.) Puppetmasterd server: We have also to regen the CSR from the existing cert (assuming our fqdn for our cert is correctly also the currently set hostname)
cd /etc/puppetlabs/puppet/ssl
openssl x509 -x509toreq -in certs/foremanDOMAIN.pem -signkey private_keys/foremanDOMAIN.pem -out certificate_requests/foremanDOMAIN_csr.pem
8.) Sign it with the new CA
cp certs/foremanDOMAIN.pem certs/foremanDOMAIN.pem.old #Backing up
openssl x509 -req -days 3650 -in certificate_requests/foremanDOMAIN_csr.pem -CA ca/ca_crt.pem
-CAkey ca/ca_key.pem -CAserial ca/serial -out certs/foremanDOMAIN.pem9.) Validating that puppetmasted key and new certs are matching (so crt and private keys are ok)
( openssl rsa -noout -modulus -in private_keys/foremanDOMAIN.pem 2> /dev/null | openssl md5 ; openssl x509 -noout -modulus -in certs/foremanDOMAIN.pem 2> /dev/null | openssl md5 )
10.) restart puppetmasterd
systemctl restart puppet
** so far did not work ***
any help appreciated. We have no foreman administrator anymore, so its just me trying to figure shit out… I may try the cert update again and then look at the logs to see why i cant log in…

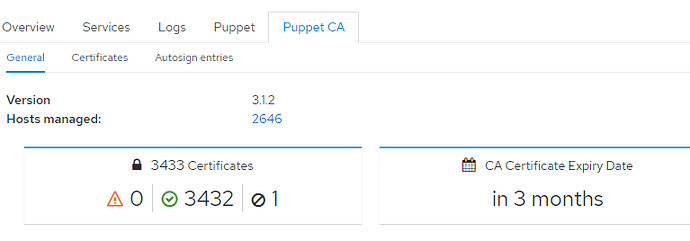
 maybe this has done it.
maybe this has done it. It would be nice if foreman had a way to disable certificate checking, incase problems like this occured.
It would be nice if foreman had a way to disable certificate checking, incase problems like this occured.