Hi!
I would like to add support for bolt tasks to the remote execution architecture in foreman.
What’s bolt?
An open source tool from same people as Puppet ( Welcome to Puppet Bolt®). It supports runnings commands (shell or powershell), scripts (anything that’s executeable), tasks or plans.
What’s a task?
A task is anything that’s executeable + a json file describing the purpose of a task and optional input parameters with datatypes. Tasks return json. bolt has a CLI interface and an API, no web UI. bolt can use different transport protocols, ssh and winrm are available by default. It has a plugin system.
Rationale:
Puppet Enterprise (costs per node per year) has a Web UI to start tasks. I think it would be a great fit for the foreman UI to also support bolt tasks. bolt tasks are heavily used within the Puppet Enterprise and Puppet Opensource ecosystem for orchestration. For example OS patching whole clusters or doing software rollouts.
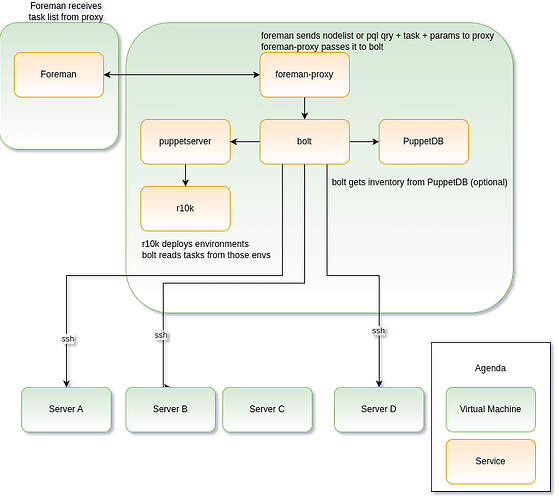
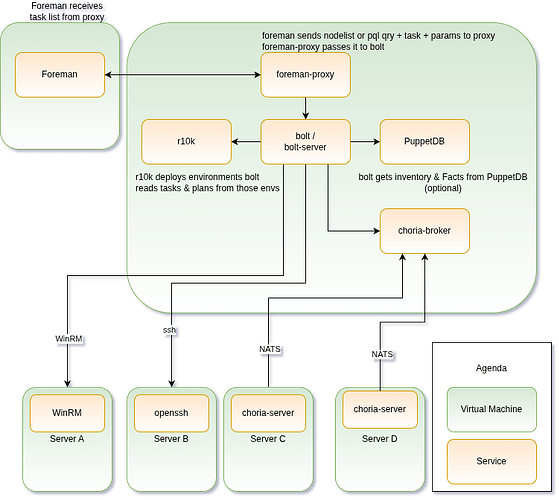
I came up with a very professional drawing:
I don’t understand all the pieces in the remote execution architecture yet, but my rough ideas:
- There’s already support for remote execution via ssh, triggered from a system running foreman-proxy. I want to build upon this / extend it.
- Foreman supports different job categories, ‘bolt tasks’ could be another one?
- foreman asks foreman-smartproxy which talks to a local bolt-server to get a list of tasks + description, as an alternative to the current job templates.
- After a user selected a task, they can enter the different parameters, data is send to the smartproxy and then to bolt-server
- bolt reuses the ssh authentication credentials from the ssh backend
- all targets, where a task was executed, return structured data, bolt-server itself returns a result set to foreman-proxy which in turn hands it over to foreman
Those are some rough ideas that I want to work out in the next time. If you’ve any ideas, feedback, concerns, let me know.