Navigating to /users/extlogin redirects back to users/login and produces an “SSO Failed” error in production.log, but does not show any information that might point to why the SSO failed. Currently I have set up a Keycloak realm which allows login via Microsoft SSO and have linked it to Foreman as per the instructions in the manual. Any input on how this could be resolved would be much appreciated.
Log extract below for clarification
2021-01-11T10:15:10 [I|app|f96b32d5] Started GET "/users/extlogin" for 127.0.0.1 at 2021-01-11 10:15:10 +0000
2021-01-11T10:15:10 [I|app|f96b32d5] Processing by UsersController#extlogin as HTML
2021-01-11T10:15:10 [W|app|f96b32d5] SSO failed
2021-01-11T10:15:10 [W|app|f96b32d5] falling back to login form
2021-01-11T10:15:10 [I|app|f96b32d5] Redirected to https://[FOREMAN]/users/login
2021-01-11T10:15:10 [I|app|f96b32d5] Filter chain halted as :require_login rendered or redirected
2021-01-11T10:15:10 [I|app|f96b32d5] Completed 302 Found in 1ms (ActiveRecord: 0.0ms | Allocations: 438)
2021-01-11T10:15:10 [I|app|f91417f3] Started GET "/users/login" for 127.0.0.1 at 2021-01-11 10:15:10 +0000
2021-01-11T10:15:10 [I|app|f91417f3] Processing by UsersController#login as HTML
2021-01-11T10:15:10 [I|app|f91417f3] Rendering users/login.html.erb within layouts/login
2021-01-11T10:15:10 [I|app|f91417f3] Rendered common/_login.html.erb (Duration: 0.1ms | Allocations: 112)
2021-01-11T10:15:10 [I|app|f91417f3] Rendered users/login.html.erb within layouts/login (Duration: 0.8ms | Allocations: 292)
2021-01-11T10:15:10 [I|app|f91417f3] Rendering layouts/base.html.erb
2021-01-11T10:15:10 [I|app|f91417f3] Rendered layouts/base.html.erb (Duration: 1.0ms | Allocations: 1040)
2021-01-11T10:15:10 [I|app|f91417f3] Completed 200 OK in 4ms (Views: 2.5ms | ActiveRecord: 0.0ms | Allocations: 2512)
Hello,
I am sorry for this inconvenience, although I have a few suggestions that you can try out and let me know the output of:
- In Keycloak, can you paste the relevant redirect urls that are mentioned by you?
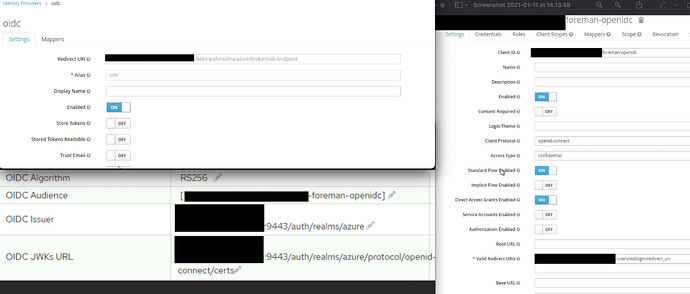
- Can you please take a screenshot of your foreman OIDC related settings here (make sure to blur the domain
 )
)
Also, feel free to ping on #theforeman-dev, freenode channel on IRC.
Thanks,
1 Like
Hi rabajaj, thanks, I am a new user so have had to work around the attachment limit by screenshotting a view of all 3 images but please see below.
Edit: Should have added, Foreman, Puppet and Keycloak are running on the same VM, hence using 9443 for Keycloak as the default 8080 and 8443 are already in use
Yup, I can see one possible place which can cause the error:
In the Valid redirect URIs section can you add another redirect URI without the /redirect_uri in the URI. So you URL should look like https://domain.com/users/extlogin
You might already know this, just mentioning it for caution  Please note there is no
Please note there is no / in the end of the URI.
Click save.
Thanks,
1 Like
Afraid that hasn’t appeared to do anything. If I navigate to /auth/realms/azure/account then I can log in and link an account to AAD but nada with Foreman sadly. Thanks for your help so far
Just noticed, a change was made at some point changing the oidc_audience to an array rather than single string, would this have anything to do with it? My main issue though was the fact that Foreman logs don’t show anything pointing as to why SSO failed. Is there a way to add more verbose logging?
Hello,
Can you add the Valid redirect URI as requested earlier and attach the result here. Also, Have you filled in the option for logout url?
Thanks,
I spoke to tbrisker on the IRC channel who helped me find the issue. We looked at a couple things and he suggested that it was likely to be an Apache config issue. He was correct; on Debian-based distributions Apache is installed to /etc/apache2, while on RedHat-based distributions it is installed to /etc/httpd. The foreman-installer package accounts for this and installs Apache to the correct folder. However, the keycloak-httpd-client-installer does not account for this difference and just installs to /etc/httpd, so moving the config files from /etc/httpd/conf.d/ over to /etc/apache2/conf.d/ it now takes the user to /users/extlogin with the prompt to sign in via Keycloak.
2 Likes

 )
)