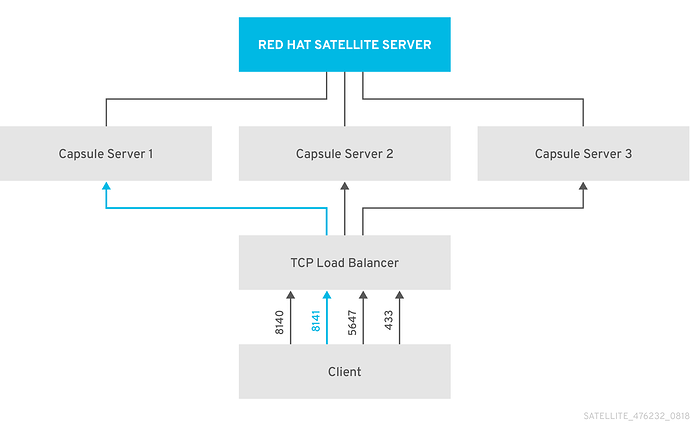
Global registration is missing an option to use load balancer when registering and configuring new hosts. For some users [0] this is considered as a blocker for moving to the global registration from other client tools that are going to be deprecated in upcoming releases.
Implementation
Foreman
In the Smart Proxy field list load balancers that are associated with them. Selected LB URL will be then used in the registration command and in the templates for subscription-manager configuration. List of load balancers for smart proxies could be loaded the same way as we load features right now.
For users that didn’t update smart proxy configuration or don’t have a version that supports it yet we can display a simple text field for load-balancer URL where they can put the URL they want.
Smart Proxy
Store list of load balancers in yaml config file. It can be either in settings.yml or it can be a new file.
Foreman installer
New option for adding / removing load balancers
User scenario
- Add load balancer(s) to the Smart Proxy
- Refresh Smart Proxy in Foreman
- Generate registration command with LB
- Register host with it
- ???
- Profit
Having covered this scenario would help us to improve user experience, moves us closer to deprecation of other registration clients and having information about load balancers in Foreman could be used in other components, like for example in provisioning.
[0] 2105995 – Need Proper Registration method in Load-balancing capsule setup for a clients
[1] Satellite docs - Configuring load balancers