The problem
As a Katello user with custom (non-Red Hat) products, I need a way to restrict my hosts’ access to those products when I want to.
Background
Historically, the tools available to accomplish this restriction have been the following:
- Don’t attach a subscription to the host or activation key for any products for which you want to restrict access.
- Use content views and lifecycle environments to filter which products are available to hosts.
- Use composite content views to combine content from different CVs
- Use repository set overrides (“Override to disabled” / “Override to enabled”) for any repositories you wish to restrict further. You can do this for both activation keys and individual hosts.
- Use the repository-level options Restrict to Architecture and Restrict to OS Version to further narrow down which repositories are available. (note: Restrict to Architecture works with CentOS and other non-RHEL systems, but Restrict to OS Version only works with RHEL.)
- With Katello 4.6, Simple Content Access is now the default for new organizations.
- In the future, entitlement-based subscription management (in other words, not using SCA) will go away entirely.
- For organizations using SCA, restricting content through subscription attachments or lack thereof is not available because subscription attachment is not a thing anymore and custom products are always enabled by default.
You may at this point be thinking, “Why not just give us access to the Candlepin product content parameter that allows you to set a repository’s default enablement on an individual repo basis?” Two reasons:
- When changing this for a given repository, it would affect all hosts which have access to that repository, immediately. There’s no way to make it affect “just new products” or “just hosts registered after this,” etc. This is why we had to revert that change originally in 2020.
- It would be giving users yet another configuration option. We’ve been given the directive “don’t add any more of those.”
So we got together and brainstormed some other ways we could make SCA easier with custom products:
Proposed improvements
- Automatically add disabled overrides for custom products to any newly-created activation key.
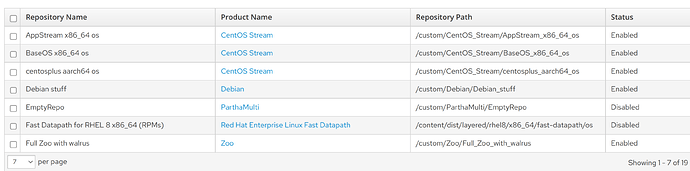
So, after creating a new AK, instead of this
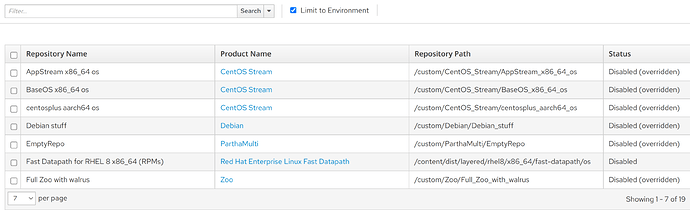
it would look more like this:
And of course, you would then be able to remove any of the overrides that were automatically added, if desired.
- Add a host bulk action to ‘Override all custom repositories to disabled.’ This would be easy to add to the individual host page as well, but would probably be more useful when performing on multiple hosts at a time.
Comments on the proposed improvements above are welcome, as well as lively discussions ![]()